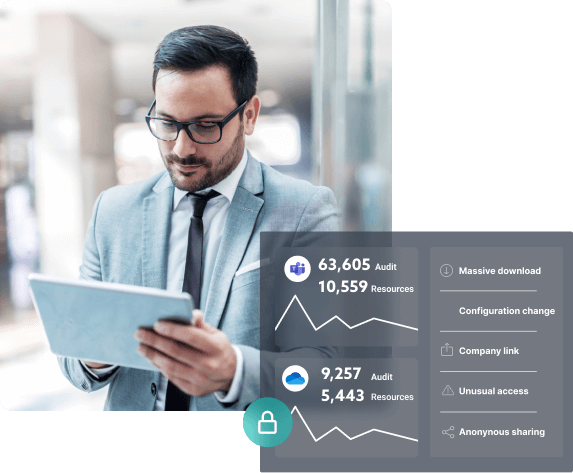
Improve visibility
Run analyses with just one click. Access critical information fast.
The Challenge
Knowing who is doing what, accessing what, and sharing what with whom.
Audits and reporting
Access the right information
The operations carried out (access, permissions, sharing, configuration) are collected, classified, and recorded in the history. You can see an accurate picture (global, specific analyses, by organization, etc.) on demand with just a few clicks.
Forensic
All information in a centralized location for investigation
When investigating or preventing, you can efficiently trace the access and configuration operations carried out anywhere in your system.
Control and compliance
Keep your platform safe and up-to-date
Improve data governance, compliance, access recertification and adherence to corporate data security policies.

Pain points
Resolve information access issues
WHY CHOOSE IDECSI?
Improve your visibility and analytics capability
Save time and optimize resources
Free team members from this time-consuming step, empowering them to effectively conduct their own analyses.
Take action more efficiently (processing time, incident response, reactivity).

Improve user visibility
Each user has a personal security assistant to monitor and control their data security.
Give your users the power to control their own data: Who does what? Who accesses what? They can be involved in protecting their own data.
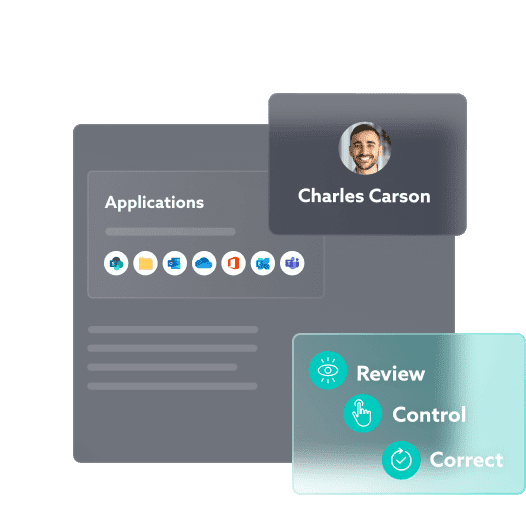
IDECSI, EASE OF USE AND EFFICIENCY
The platform that speeds up access to information
With continuous monitoring of access, permissions, sharing and configuration, and an easy-to-use platform, you can instantly access the most important information in any environment. Identify suspicious or malicious actions or configuration changes.
Pre-designed filters and analysis options
Consolidated, centralized data
Organized, pre-processed logs
Power BI reports
One-click audit
Reporting/BI security
Forensic
Rights review

Other solutions
Effective solutions for all your needs
Data protection:
Let’s talk about your project!