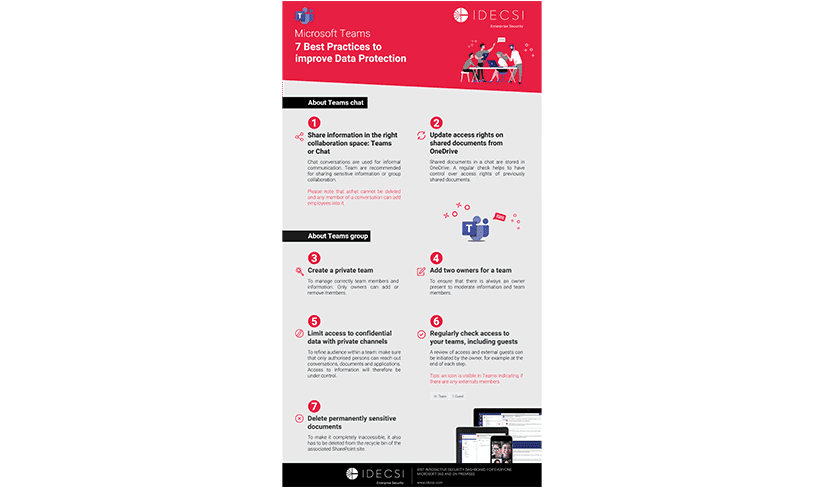
Increase detection capability
Detect suspicious or malicious activities and human errors even those with very weak signals, thanks to a powerful real-time alerting system and the involvement of your users.
The Challenge
Identify dangerous actions and prevent risk
Key threats
Detect the most critical threats immediately, as they occur: concurrent access, identity theft, brute force attacks, data exfiltration, mass deletion, successful phishing, etc.
Weak signals and internal risks
Distinguish between what is legitimate and what is not.
Identify malicious and inappropriate behavior, human error and malicious lateral movements.
User
Benefit from involving all employees in protecting the company.
Increase your detection and reaction capacity.
Reduce resolution time.

PAIN POINTS
Reliability of detection capabilities
WHY CHOOSE IDECSI?
Improve the detection of security breaches
Improve the relevance of alerts
Reduce false positives with a smart system. Every change is tracked and every threat is catalogued and identified, generating only relevant alerts identifying critical, malicious behavior.
Your users are notified of suspicious behavior
Save time on troubleshooting and remediation, as users validate the action or confirm the problem.
Improve event management efficiency while reducing costs.
IDECSI, ADVANCED AND UPGRADED DETECTION
The first detection system interacting with users
You increase your capacity to reliably detect security breaches (malicious access, sharing or configuration, etc.) and reduce the risks inherent in collaboration tools.
Real time
Native O365 use cases
Operational immediately
Behavior analysis
Embedded threat models
Customised monitoring and protection
Real-time alerts
Smart remediation

Other solutions
Effective solutions for all your needs
Data protection:
Let’s talk about your project!