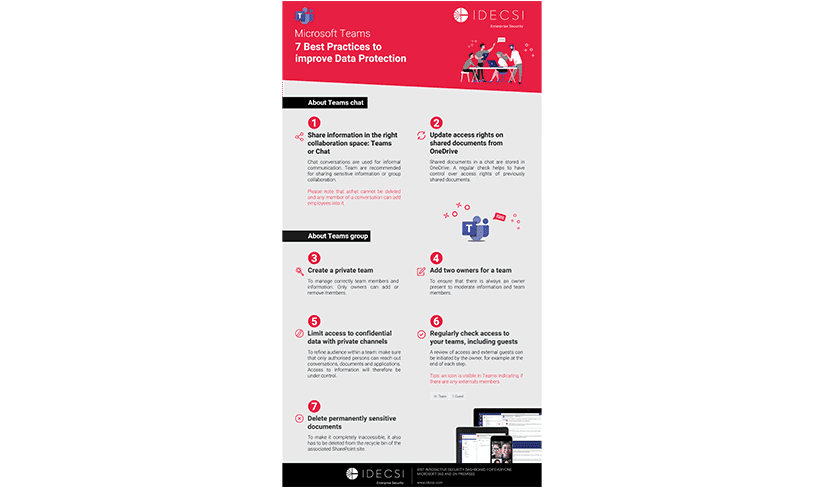
ADVANCED MONITORING
Maintain control over your data
An all-in-one tool that strengthens the key functions of detection, monitoring, audit, and remediation for even greater protection.

PATENTED TECHNOLOGY
INTUITIVE
NO INFRASTRUCTURE
REAL TIME
ADVANCED MONITORING
An expert monitoring platform for M365 and on-premise deployments
Benefit from a comprehensive tool with 4 key capabilities: detection, monitoring, auditing and remediation.
Automate alerts about sensitive data. Schedule permission reviews.
Reduce the number of people responding to security incidents by only involving the right people.

REAL-TIME MONITORING & AUDITING
Keep control over access, permissions, sharing, and configurations
Operational security teams have a complete monitoring interface where data is consolidated and available in a single location.
Immediately view permissions, configurations, delegations, and accesses. Easily initiate audits of one or more user accounts.

REAL-TIME ALERT & DETECTION
Identify any intrusion or malicious act as soon as it occurs
The preconfigured threat models ensure no unauthorized access or configuration escapes your notice. When an alert is raised, it can be sent to infosec teams, to the SOC, or integrated into a SIEM. It can also be sent directly to users so it can be addressed quickly.
Improve the reliability and scope of your detection capabilities.

AUTOMATION
Orchestrate and automate security operations
The IDECSI platform helps manage security of access and permissions. It integrates automatic recertification and remediation mechanisms. Optimize your response time and ability to react to security incidents.
Improve the productivity and effectiveness of your teams.

USER INVOLVEMENT
Connect your security mechanisms with your users
When connected to other IDECSI solutions, Advanced Monitoring helps correct and remediate problems as fast as possible.
All normal events are filtered and processed by IDECSI and validated by users.
Optimize all security processes by involving your users.

BENEFITS
An expert administration platform
INCREASE THE CAPABILITIES OF YOUR SOC/SIEM
Eliminate false positives, improve reporting of actual incidents and resolution of alerts.
Enrich your SIEM solution with more qualified alerts.
IMPROVE YOUR ROI
Greatly reduce processing and analysis costs. Help security and SOC teams focus only on real security incidents.
INVOLVE YOUR USERS
Your team members will be more aware and empowered. They can immediately validate or raise security alerts. Shorter resolution times and increased detection capacity.
COMPANIES STATE THEY HAVE EXPERIENCED AT LEAST ONE CYBER ATTACK IN 2020 – *CESIN “BAROMETER OF COMPANY CYBERSECURITY”
Activate real-time detection and alerts for your data
IDECSI’S SOLUTION
User-connected platform
The first security platform that gets users involved with the major security features, thus ensuring a high level of protection.
The solution uses a three-pronged approach:
OF CYBERATTACKS ARE CAUSED BY HUMAN ERROR*
OF EMPLOYEES ARE CONCERNED ABOUT THE SECURITY OF THEIR DATA*
OF CISOs CONSIDER SHARING MANAGEMENT BY EMPLOYEES TO BE A MAJOR SECURITY RISK*
Advanced Monitoring
An all-in-one tool that combines detection, monitoring, auditing and remediation.
*Accenture “State of cybersecurity” – Report 2020
My Data Security
A dashboard for users to track access, permissions and sharing of their data.
*IFOP survey “Les salariés et la sécurité de leurs données” – 2019
Permission Explorer
An intuitive platform for analysis and supervision.
*CESIN “Barometer of company cyber-security” – 2021
Our articles
How to improve data management
Data protection:
Let’s talk about your project!