Automate permissions and sharing reviews
Dramatically improve your recertification processes with effective user engagement, automation, and fine-grained data analysis.
The Challenge
Data governance, access and sharing
Continuous control
Manage access, permissions and sharing efficiently
Optimize permissions review processes by scheduling periodic user campaigns with one click. Reduce the risks associated with human error in collaboration tools.
Compliance and recertification
Keep your platform safe and up to date
Improve data governance, compliance, and adherence to corporate data security policies.
User governance
Involve users proactively
Users have become self-sufficient in data management. They are the ones best placed to identify and correct access, permissions, and sharing issues affecting their information.

Pain points
Access review: a complex and tedious project
WHY CHOOSE IDECSI?
Make users an active part of access review
Give your users the right tools
IDECSI has created a clear, personalized dashboard so that each employee – the essential element in any permissions review – can easily monitor their own access, permissions, and sharing in real time. By providing them with visibility and simplifying the access validation process, employees are more empowered and aware of data protection.
Automate remediation processes
Keep control over access, permissions, sharing, and configuration affecting your data.
Reduce the cost of recertification campaigns by automating the entire process.
So you can focus on what you do best and say goodbye to human error.
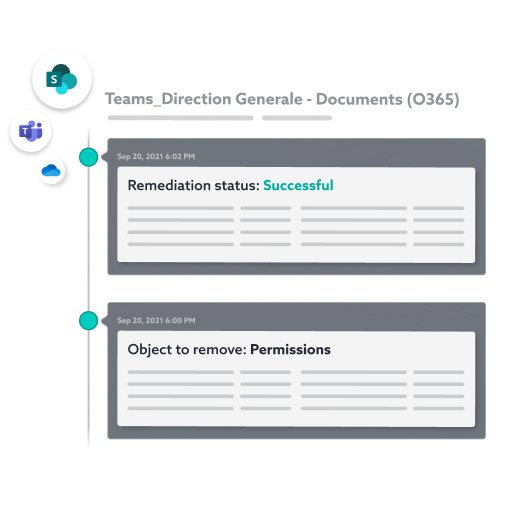
Save time on your remediation actions
Technology that revolutionizes access and sharing confirmation
Use a single solution to simplify your authorization reviews by automating the process and enabling immediate correction by employees.
Consolidated view of accesses and shares
Dynamic user interface
One-click campaigns
Automated remediation
Audit
User dashboard
Planning
Smart remediation

Other solutions
Effective solutions for all your needs
Data protection:
Let’s talk about your project!