Improve your remediation capability
Use automated remediation to correct malicious or dangerous operations or human errors as quickly as possible, with the help of your team.
The Challenge
Reduce remediation time
Incident response
Reduce the time taken to resolve a threat
Immediately stop a security breach: fraudulent access, brute force attempt, or data exfiltration.
Remediation plans
Carry out remediation quickly
Remove and clean up compromized rights and permissions. Drive recertification and remediation campaigns with just one click.
Under control
Set up a routine for supervizing and correcting data
Give your employees the resources to control and update access, permissions and sharing affecting their data. They’re in control.

Pain points
Solve security and remediation issues
WHY CHOOSE IDECSI?
Increase your risk response capability
Remediation by users
Your users manage their data, including permissions update. They can group or delete sites or member lists, manage sharing links, etc.

Automate remediation processes
Keep control over access, rights, sharing, and configuration affecting your data.
Reduce the cost of recertification campaigns by automating the entire process.
Focus on doing what is essential.
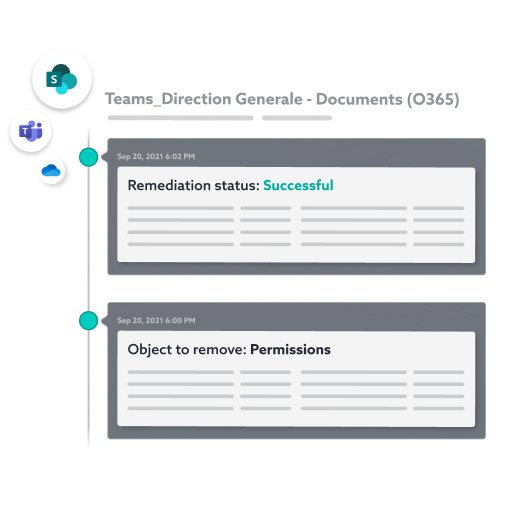
COLLABORATION ACTIONS FOR ENHANCED SECURITY
Automated remediation by users
IDECSI’s remediation leverages user connectivity and real-time alerts to manage access, permissions and sharing and resolve security incidents automatically.
Centralized view
Machine learning
Monitoring and reporting
User involvement
Audit
User action
Management
Under control

Other solutions
Effective solutions for all your needs
Data protection:
Let’s talk about your project!