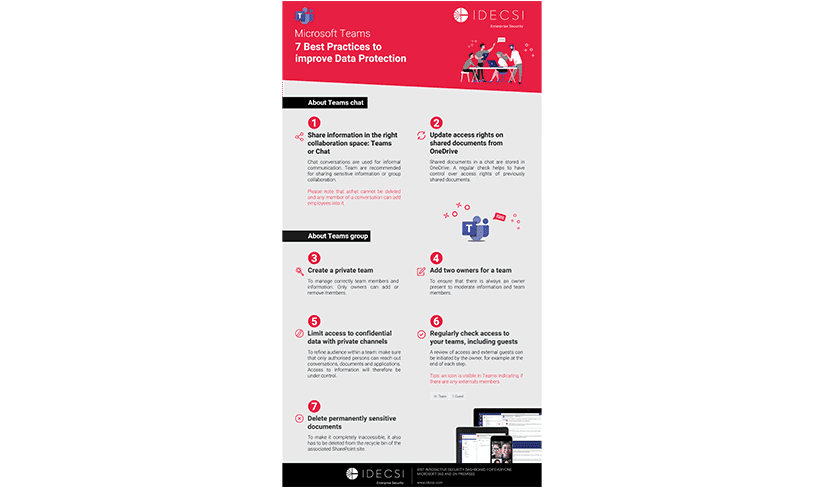
Strengthen the security of sensitive data
Enable personalized monitoring and maintain full control over the operations and access affecting your most essential data.
The Challenge
Supervizing sensitive data
Governance
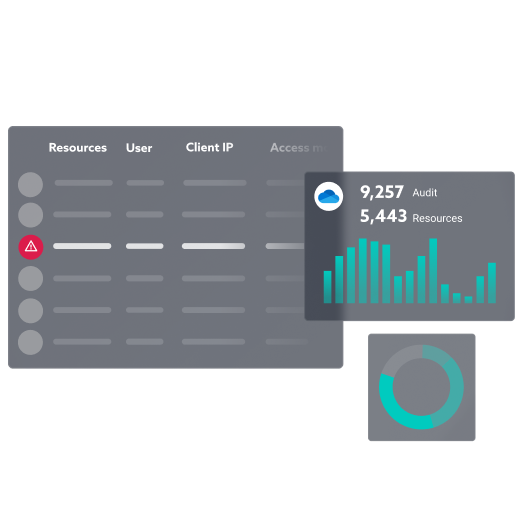
Access information about your sensitive data quickly
Where is it? Who is accessing or sharing it?
Clear analysis by label (MIP classification), by BU, by user profile, etc.
Protection and correction
Advanced monitoring and tracking for effective protection
Enable dynamic monitoring of SharePoint Online groups, Microsoft Teams, OneDrive for Business folders, shared files, and critical and confidential e-mail inboxes.
Automate data protection with Microsoft Information Protection integration.
Awareness-raising
Involve and empower your employees
Improve visibility for users: who is accessing their sensitive data? Who has permissions?
Notify owners of suspicious activity. Reduce human error and the risk of incidents.

Pain points
Protect strategic data and users from exposure reliabily and efficiently
WHY CHOOSE IDECSI?
Improve access and sharing management for your sensitive data
Focus your efforts on high-risk operations
Thanks to an automatic learning phase, each user and data source is monitored individually.
Guarantee integrity by immediately being informed of any important change or dangerous configuration.
Users are empowered
Improve adoption of Microsoft 365 collaboration tools. Microsoft Teams, SharePoint Online group owners have the resources to manage the most critical data.

IDECSI, AN AUDIT AND SUPERVISION PLATFORM
Customized protection
Control the security of your data and your key users.
User engagement
Real time
Automated remediation
One-click audit report
Advanced and personalized monitoring
MIP Integration
Real-time notification – Alert answer
User dashboard

Other solutions
Effective solutions for all your needs
Data protection:
Let’s talk about your project!