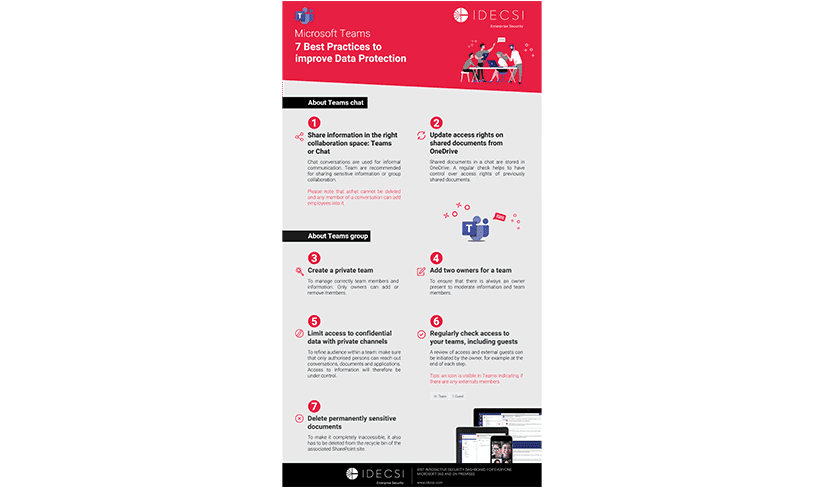
Involve your users
Increase the user’s role in protecting data and collaboration tools by involving them in the security system and allowing them to control their data.
The Challenge
Make users responsible for data security
Reduced vulnerabilities
Ensure users are aware of the situation
Avoid the serious consequences of successful phishing, human error, suspicious delegation, access to sensitive data, anonymous sharing, etc.
No limitations
Easy of use encourages better security
Be better informed. Quicker, clearer access to information for users and infosec teams contributes to more effective digital security suitable for the challenges of the Digital Workplace.
Trust and adoption
Improve risk awareness and knowledge of the tools.
Increase user confidence with a consolidated, personalized dashboard and improve the use of digital tools.

Pain points
Make data security accessible to all
WHY CHOOSE IDECSI?
Successfully engage users in security
Improve user experience
With personalized protection and a customized dashboard, each user can control access, permissions, and sharing of their data. They can be notified about suspicious activity and review current authorizations.
Unprecedented visibility for engagement and a positive experience.

Optimize the security system
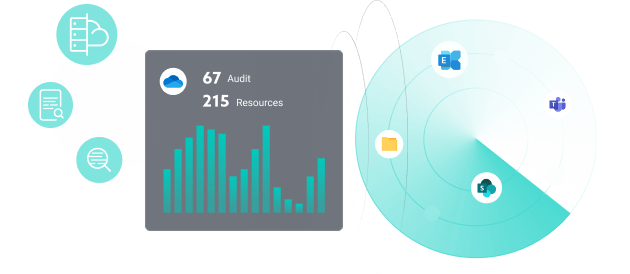
IDECSI has developed a solution that detects unauthorized access or suspicious data operations, as well as malicious configuration changes.
Interacting with users, it minimizes detection and resolution times.
Distributed detection also improves the efficiency of the SOC, allowing the security team to focus on high-risk events and optimizing its resources.
IDECSI, A NEW EXPERIENCE IN DIGITAL SECURITY
Your users interact with the security system, offering significant advantages
Thanks to IDECSI, employees have the resources to take action. They enhance the capabilities of the monitoring platform, contributing to security alongside infosec teams.
Easy to use interface
Effective engagement
Autonomous protection
Short processing circuit
User dashboard
Accessible via a website, mobile application, or directly by e-mail
Personalized notifications
Rights review
Remediation

Other solutions
Effective solutions for all your needs
Data protection:
Let’s talk about your project!