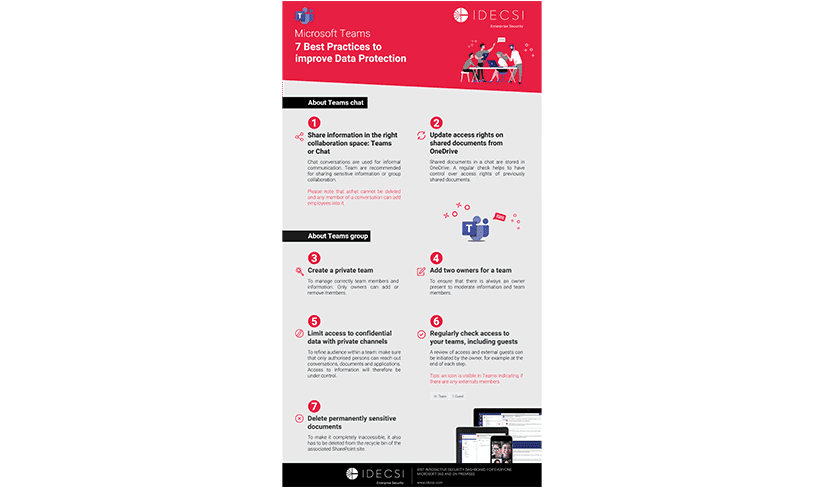
MyDataSecurity
Empower users to manage data access and sharing efficiently
With MyDataSecurity, an easy-to-use interface, users have the right tool to control and manage their data and collaborative workspace.

VISIBILITY ON PERMISSIONS AND WORKSPACES
MANAGE DATA ACCESS & SHARING LINK
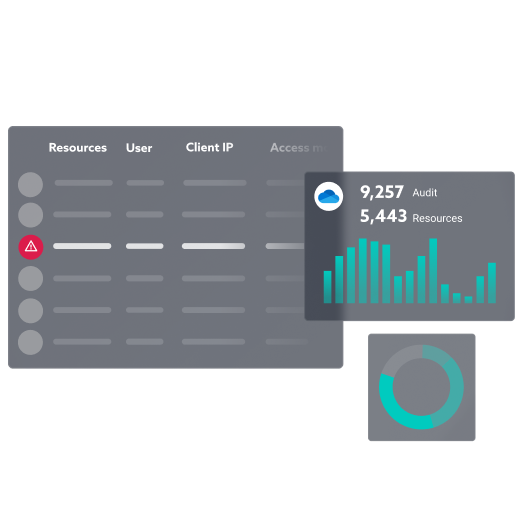
POINTS OF ATTENTION
INTUITIVE INTERFACE
MYDATASECURITY
Strong, collective protection that is highly cost-effective
Improve visibility for the data owners.
Allow data owners to manage external access, sharing link, group members and get effective permission management.

Watch the MyDataSecurity video


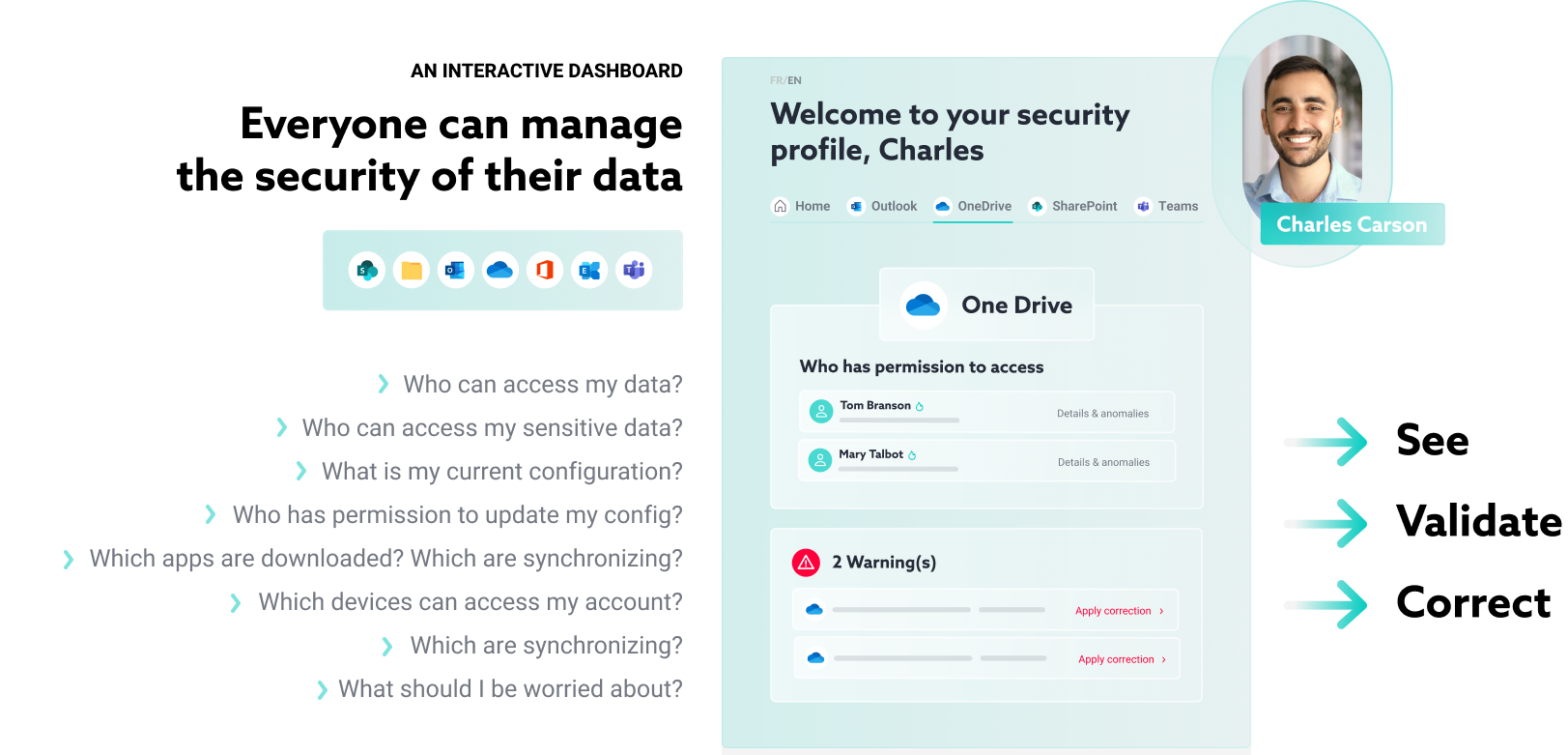
CENTRALIZED AND PERSONALIZED DASHBOARD
Provide every user with visibility of their environment and who’s accessing their data
Each user has a personalized dashboard allowing them to monitor and visualize their data across their M365 environment: Who can access it? Who has permissions? Who is looking at and sharing their data?
Users can see, control, and make any necessary changes directly.
Simplify the security experience through a simple, user-friendly mobile and web interface.
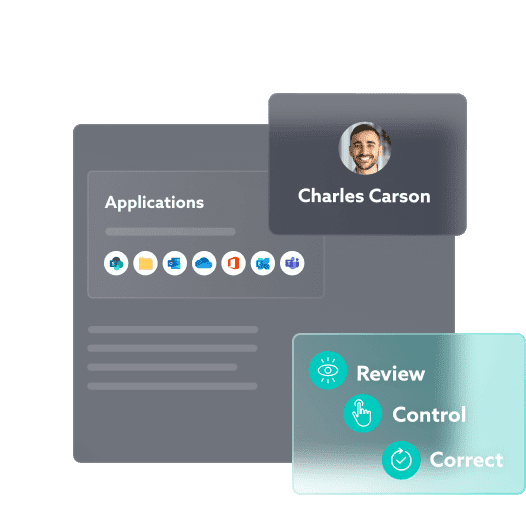
SIMPLIFIED PERMISSIONS MANAGER TOOL
Launch campaigns with a single click, using automated and centralized dashboard processing
The user is able to immediately identify any anomalies, security issues, errors, or obsolete permissions.
Thanks to MyDataSecurity, reviewing permissions and recertification becomes interactive and programmable. Performance is monitored and issues can be directly remediated by users.

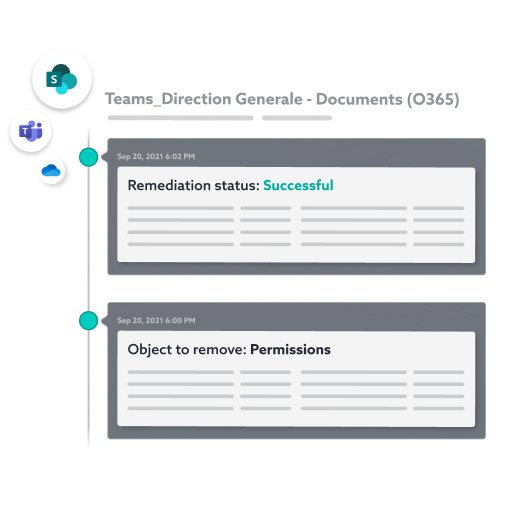
AUTOMATED REMEDIATION
Reduce incident remediation time
Notifications can be sent for any actions requiring verification, further increasing the level of vigilance and reducing response time (new permissions, new device, new rule, etc.).
The platform can automatically perform remediation operations under supervision, but without requiring intervention by IT administrators or infosec teams.
INTEGRATED WITH EXISTING SECURITY TOOLS
Strengthen security across the company
Infosec teams define MyDataSecurity parameters: which elements are visible to users, notification policies, and remediation rules.
Connected to your SIEM, MyDataSecurity and the IDECSI platform reduce costs and improve event processing. Significant events with real risk are more clearly identified and only then are they reported. SOC teams can improve their performance: greater capacity to analyze and detect and save time by avoiding unnecessary investigations they can be self-managed by users.
AWARENESS AND COLLABORATIVE SECURITY
Data protection for and by users
EMPOWER YOUR USERS
Users help bolster security with MyDataSecurity.
Access to and sharing of their data is better managed and protected.
IMPROVE YOUR PERFORMANCE
MyDataSecurity enables ongoing, dynamic and highly precise monitoring of your organization’s digital security.
Detection and responsiveness are more accurate and faster.
GREATER TRUST
Users have greater visibility over all their resources and are better able to monitor their data.
Everything is centralized; managing and adopting new digital tools is easier than ever.
OF EMPLOYEES WANT TO BE INVOLVED IN SECURING THEIR DATA -IFOP STUDY “EMPLOYEES AND THE SECURITY OF THEIR DATA”
Empower users for more effective security
IDECSI’S SOLUTION
User-connected platform
The first security platform that gets users involved with the major security features, thus ensuring a high level of protection.
The solution uses a three-pronged approach:
OF CYBERATTACKS ARE CAUSED BY HUMAN ERROR*
OF EMPLOYEES ARE CONCERNED ABOUT THE SECURITY OF THEIR DATA*
OF CISOs CONSIDER SHARING MANAGEMENT BY EMPLOYEES TO BE A MAJOR SECURITY RISK*
Advanced Monitoring
An all-in-one tool that combines detection, monitoring, auditing and remediation.
*Accenture “State of cybersecurity” – Report 2020
My Data Security
A dashboard for users to track access, permissions and sharing of their data.
*IFOP survey “Les salariés et la sécurité de leurs données” – 2019
Permission Explorer
An intuitive platform for analysis and supervision.
*CESIN “Barometer of company cyber-security” – 2021
Our articles
How to improve data management
Data protection:
Let’s talk about your project!