A global platform
PRECONFIGURED
REAL-TIME
CENTRALIZED INFORMATION
HYBRID
The IDECSI monitoring platform collects and analyzes access logs, technical objects as well as the permissions and authorisations established for each file. The platform covers all users and resources (collaboration, messaging, storage) in the cloud and on-premise to provide advanced protection for your environments.
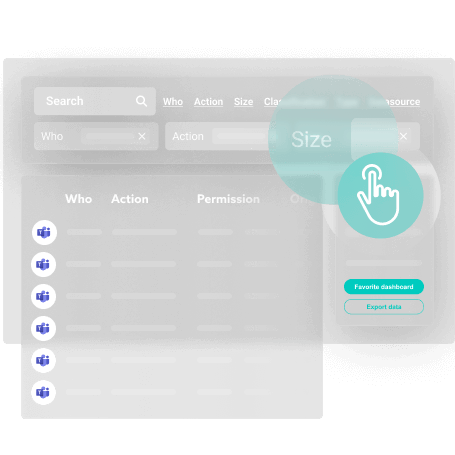
Supervise access, permissions, sharing and configuration of your data and improve your visibility in a single interface.